Private messengers: what can they really see?
This article aims to provide a fair and thorough comparison of the current private messaging apps in terms of their privacy, security, and anonymity†. However, it must be abundantly clear that this post is written by Status (one of the above messengers). We strongly encourage you to verify our sources, do your own due diligence, and correct us if we are wrong.
†For the purposes of simplicity for the average reader, anonymity will be defined as a complete dissociation of one's chat identity and their true identity.
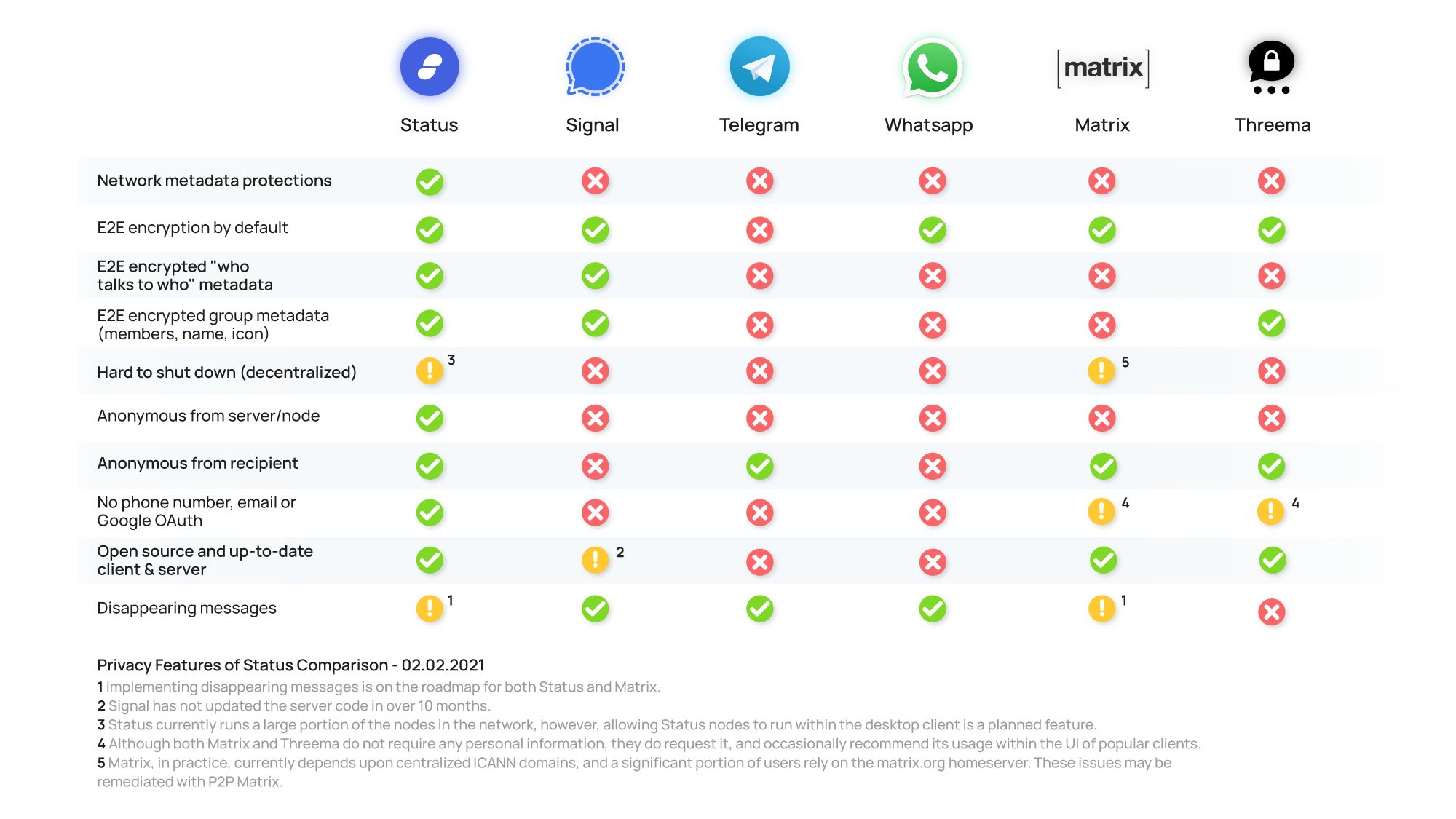
Not much. Your messages, attachments, calls, sender metadata, group chats and group metadata are all end-to-end encrypted. However, Signal (and Amazon) can infer who talks to who with a fair degree of accuracy by analyzing the network traffic. Signal is the only entity that runs the Signal servers, and they host all such servers on Amazon Web Services. Here is a simple breakdown of what the network traffic could look like if Alice (1.1.1.1) sent a message to Bob (2.2.2.2):
08:23:02 — IP Address 1.1.1.1 sends 512 bytes to Signal's server.
08:23:04 — IP Address 2.2.2.2 receives 512 bytes from Signal's server.
This is what Jeff Bezos can see. Now, this, on its own, doesn't necessarily mean that Alice is talking to Bob. It could just be a coincidence — Bob happened to receive a different and entirely unrelated packet two seconds after Alice sent one of equal size.
However, if this coincidence were to happen, ten, twenty or a hundred times, with packets of equal sizes going back and forth from Alice and Bob, it would soon become apparent that these two IP addresses are likely talking to each other. At this point, one simply has to ask the respective Internet Service Provider (such as Comcast or AT&T) who is behind a given IP address to uncover their legal identity.
So basically, Jeff Bezos can know who you talk to on Signal with a fair degree of accuracy via traffic analysis. This can be done even without Signal's cooperation, as Amazon has direct access to all incoming and outgoing traffic on the centralized Signal servers. In fact, Moxie Marlinspike, the creator of Signal, acknowledged this flaw in the Q&A session of his 36C3 talk "The ecosystem is moving."
If Signal were to cooperate in such traffic analysis attacks, it would become much easier, as Signal does have access to the recipient metadata (but not sender metadata). In other words, they can see who the envelope is addressed to, but not who it came from. This, in addition to the traffic analysis, would allow Signal to infer nearly all the sender/recipient metadata, in addition to some of the group metadata.
No. You are required to provide your phone number — which, in many parts of the world, is synonymous with providing your government-issued ID. In addition, Signal will leak your IP address to your contacts that call you by default (you can change this in the settings by enabling the option "Always Relay Calls"). Signal also has the technical capability of associating your IP address and your Signal account (but they probably don't do this). This means that even a burner number isn't enough for total anonymity if you assume the Signal servers are malicious or compromised.
It is worth noting that Signal has never claimed to be an anonymous tool. These points do not detract from the fact that they do care about your privacy — they are simply approaching it in a different manner.
If you don't have any faith in the US government, the answer is yes. If you do, the answer is probably not. Signal is the sole operator of the Signal servers, and they are based in the United States. There is no federation, and there is no peer-to-peer architecture. If Signal is legally compelled to shut down their servers, that's it. All forms of communication through Signal would immediately halt. However, the likelihood of such an event is debatable, and will be left to the reader.
It would be very difficult to quickly move Signal to a different jurisdiction, as they have thus far operated under the assumption that the US will not ban them. Moxie Marlinspike lives in the US, as does the overwhelming majority of Signal's employees, and their only two legal entities were incorporated in the US. In addition, given the centralized nature of their server architecture, Signal themselves could shut down Signal (this may seem obvious, but certain decentralized architectures prevent even the creator of something from shutting it down, such as Bitcoin).
Basically everything. They can see every message you've ever sent in a group chat, most of your 1:1 conversations (not secret chats), all your contacts, your profile picture and your bio. They know who you talk to, and at what time (even if it's a secret chat!). They know the members, name, and icon of every single group (including private ones) .
This may sound completely contrary to what Telegram says. The reason is that Telegram fundamentally operates on a different trust model. They assume that you trust Telegram, but not the government.
Telegram splits up their encryption keys and stores the separate pieces in several different jurisdictions. In theory, this means that all of the jurisdictions used by Telegram would have to cooperate in order to obtain any user data. They claim this has allowed them to not release a single byte of user data. These claims, by their very nature, are unverifiable, and require that you trust Telegram. If that's good enough for you, use Telegram.
Kinda. If you trust Telegram, then Telegram can be anonymous, as you are given the option hide your phone number and use a username of your choice. If you don't trust Telegram, it is not anonymous in any way, as they will have your phone number and they can see your IP address.
Probably not. Telegram intentionally set up its legal structure to be agile and resistant to overreaching governments. If Dubai (their current jurisdiction) bans them, they would likely move to another. Dubai is a flag of convenience for Telegram. However, given the centralized nature of their server architecture, Telegram themselves could shut down Telegram.
All the metadata, but none of the content. They can see your profile picture, who you talk to, and when. They can see who is a member of a given private group, the group icon, the group name, and which members are the administrators of said group. But your messages, pictures, attachments, status updates and calls are all end-to-end encrypted.
However, it is very important to note that the end-to-end encryption of WhatsApp messages has been repeatedly compromised through unencrypted Google or iCloud backups. Although these backups are technically optionally, they are repeatedly suggested to the user with a coercive user interface. Even if you do not enable these backups, there is a good chance your conversation partner did, which compromises the integrity of the end-to-end encryption for both of you.
No. You are required to provide your phone number — which, in many parts of the world, is synonymous with providing your government-issued ID. In addition, WhatsApp logs your IP address and directly associates it with your chat identity.
Not really, given the scale of Facebook and the nature of public corporations. However, it is very likely that WhatsApp could be forced to include a backdoor into their clients. There would be no way around this, as the clients are all proprietary. With all other messaging apps in this list, one could simply download the code prior to the backdoor, build it, and run that version of the client which still correctly encrypts the messages. Decentralized messaging architectures such as Status or Matrix would be even more resilient against such coercion, as there would be no central servers to shut down.
All the metadata, but none of the content. They can see your profile picture, your private room aliases, your device names, who you talk to, and when. They can see who is a member of a given private room, the room icon, the room name, and which members are the administrators of said room. They can see who talks and when in private rooms. But your messages, pictures and files are all end-to-end encrypted by default.
Although some homeserver implementations have stopped storing this metadata by default, all homeservers still have the technical ability to access it. Some of these metadata issues may be resolved with the latest developments in P2P Matrix, but it is unclear as to whether or not this will be effective in regards to room metadata such as membership or administrator privileges.
It should be noted that the relative ease of hosting your own Matrix server diminishes the value of any metadata leaks. If all of your contacts use a Matrix server that you trust (which could be one that you host), it doesn't matter if the server can see this metadata. However, in practice, most people just use someone else's server (such as the matrix.org one).
Kinda. If you trust the federated homeserver you are connected to not to disclose your IP address, you are anonymous. If not, you are not anonymous, as the homeserver you connect to will be able to directly associate your chat identity and IP.
Although it technically is possible to host a Matrix homeserver as an anonymous Tor onion service, it is highly impractical to do so as the process has yet to be streamlined.
No. It would be practically impossible to entirely shut Matrix down. The Matrix Foundation cannot shut down Matrix. However, significant damage could be done given the current points of centralization. First, if the matrix.org homeserver were to be shut down, it would massively disrupt the ecosystem given the large portion of users that depend upon it. And second, all Matrix homeservers currently depend upon centralized ICANN domains. Both of these issues may be remediated by P2P Matrix down the line.
Some of the metadata, and none of the content. They can see who you talk to, and when, and they can trivially infer group membership as their servers have access to sender/recipient metadata. But your messages, pictures, attachments, profile pictures and calls are all end-to-end encrypted.
Kinda. If you trust Threema to not to disclose your IP address, you are anonymous. If not, you are not anonymous, as Threema has the ability to directly associate your chat identity and IP (but they probably don't do this).
If you don't have any faith in the Swiss government, the answer is yes. If you do, the answer is probably not. Threema is the sole operator of the Threema servers, and they are based in Switzerland. There is no federation, and there is no peer-to-peer architecture. If Threema is legally compelled to shut down their servers, that's it. All forms of communication through Threema would immediately halt. In addition, given the centralized nature of their server architecture, Threema themselves could shut down Threema.
Basically nothing. Your messages, attachments, sender metadata, group chats and group metadata are all end-to-end encrypted. In addition, Status provides strong network metadata protections. All encrypted messages are forwarded to every single node in the network. It is entirely impossible to determine who is talking to who when using a full node. Light clients (such as the mobile apps), although less robust, still provide reasonable network metadata protections given the distributed nature of the network (compared to centralized servers which can be trivially monitored), in addition to obfuscating the recipient metadata with the usage of bloom filters.
Status uses a purpose-built peer-to-peer messaging stack with strong privacy, security and censorship-resistance guarantees. Even if your client were to connect to a malicious Status node, your privacy would still be protected. Only a global passive adversary can infer sender/recipient metadata of Status. This could potentially be resolved with the usage of mixnets, and will be left as future work to the Vac Team.
Yes. Status nodes are entirely incapable of associating your IP address and your chat identity. In addition, you will never be asked for a phone number, email address, or any other form of personally identifiable information. Status nodes know nothing about you or the messages you send.
No. It would be practically impossible to entirely shut Status down. Status cannot shut Status down. However, significant damage could be done given the current points of centralization. Status currently hosts a large portion of the Status nodes. If all of these nodes were shut down, it would likely render the network unstable and unreliable. This is actively being worked on. Status desktop clients will eventually support the ability to run a full node which would immediately improve the decentralization of Status, and render it far more robust and censorship resistant.