Elements of Private, Secure Messaging Apps

Privacy, and the protection of this basic human right, is crucial. Surveillance is on the rise and unbalanced financial incentives are leading companies to extract as much information as possible. Now, more than ever, we need to collectively safeguard this right.
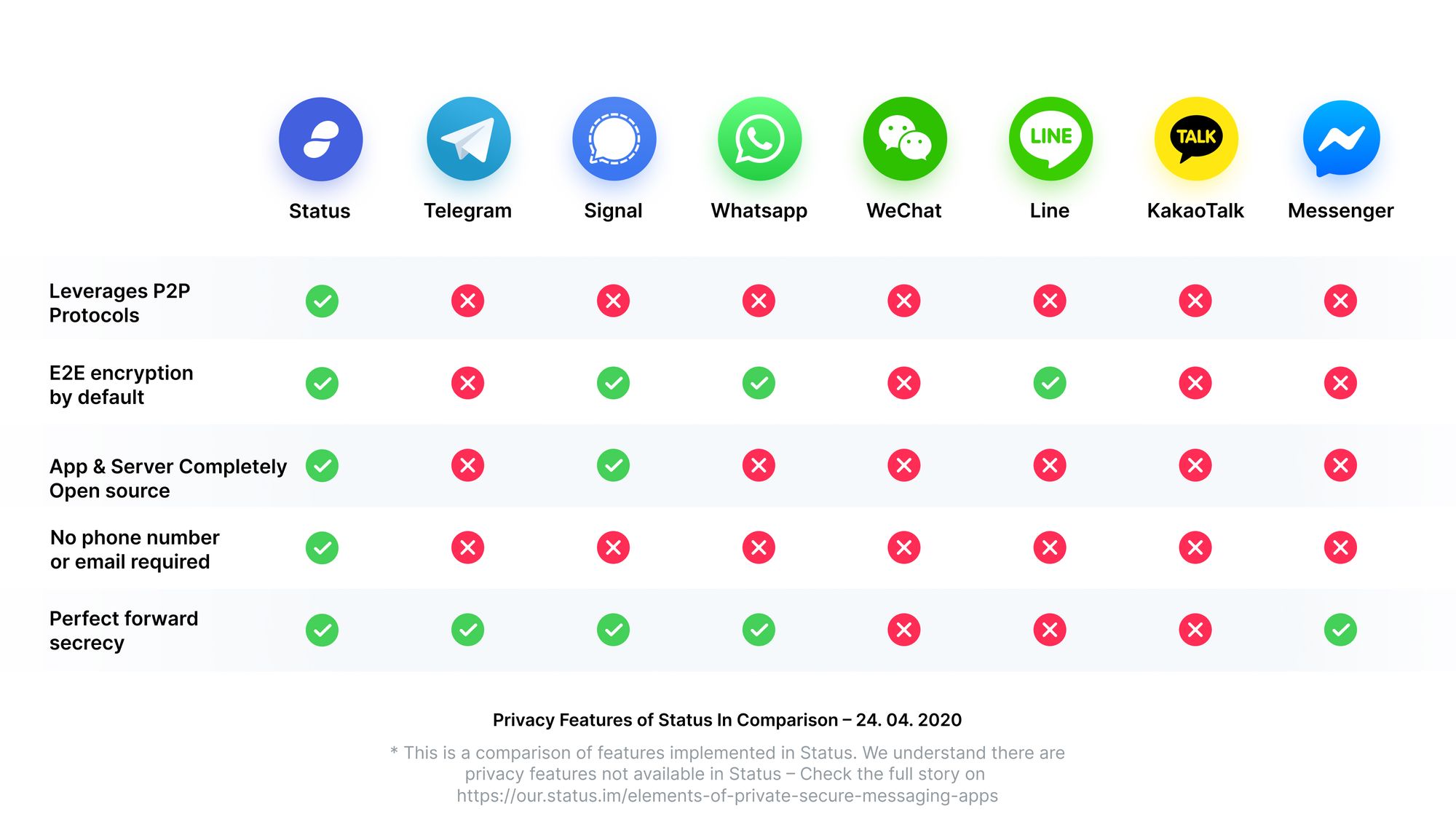
Using private messaging apps and protecting our communication from those looking to censor us or monetize our data is one way to do so. In the first article of this series we took a look at why privacy is important even if you are not hiding anything. In this article we will explore some features that we have implemented in the Status mobile app to protect privacy.
While architecting Status, these are simply some of the implementations that we deemed crucial. These are not the only elements that make a messenger private and certainly not the only way to approach a private, secure messaging app. There are talented teams around the world working on other tools designed to protect our privacy.
And it is not to say that by implementing these features, Status has delivered a silver bullet solution to privacy preservation. We are constantly evolving our tech stack and looking for new and innovative ways to deliver stronger privacy and security guarantees.
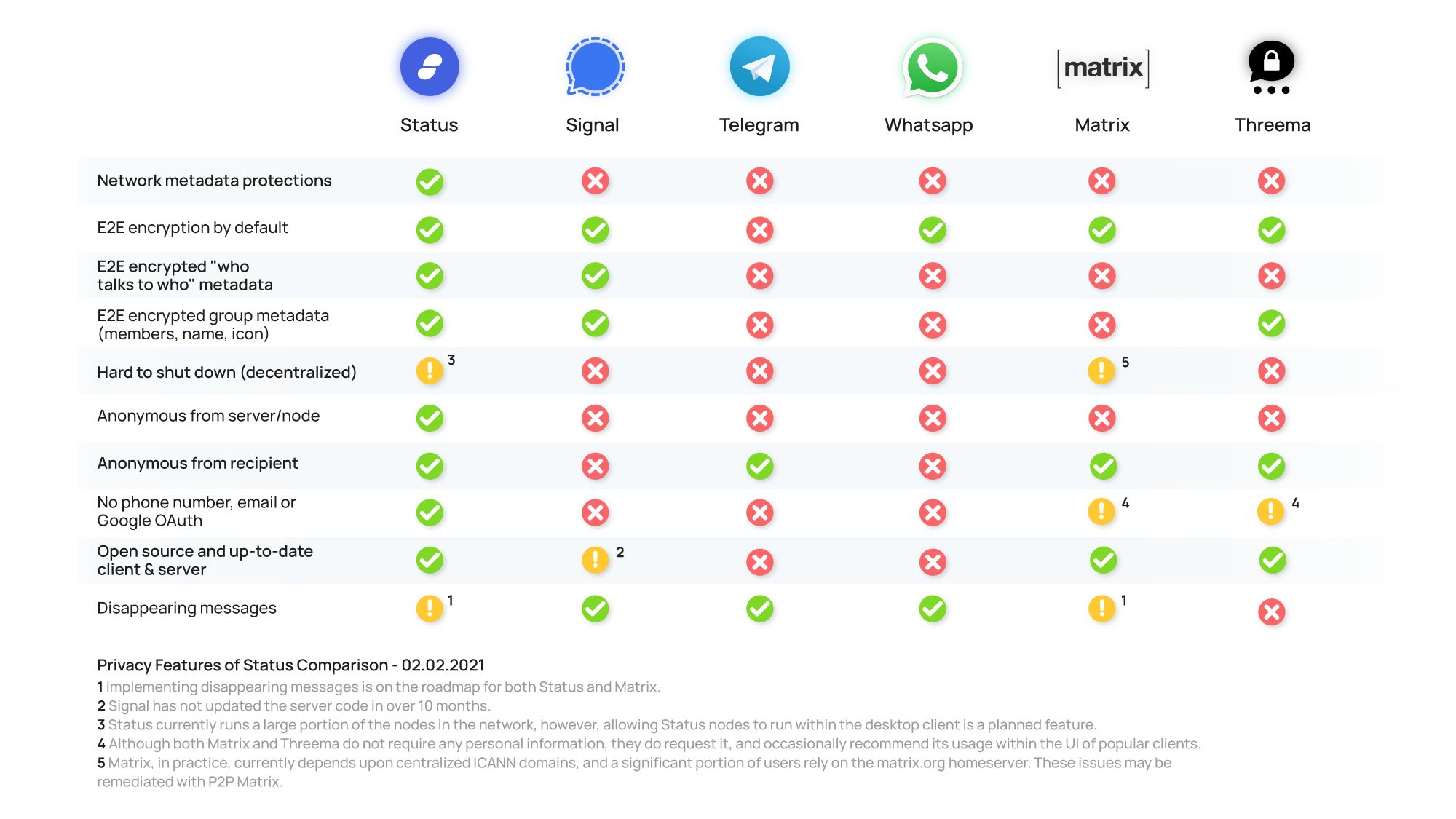
End-to-end encryption is an imperative element in the world of private messaging. Not only the ability to encrypt your messages, but enabling this feature by default across all forms of messaging is crucial. Telegram is an encrypted messaging app but only implements e2ee in certain modes of operation.
End-to-end encryption implies that your messages are locked with a key that only you and the intended recipient(s) have access to. This means that messages are encrypted and secure the entire time they are in transit.
In most of today’s internet networks, third party intermediaries pass messages from sender to receiver. End-to-end encryption protects the content of the messages from these intermediaries (and anyone else who may intercept the message) as they do not hold the necessary keys to reveal the content of the given message.
Status has implemented many of the same open source encryption algorithms developed by the talented team at Signal, which have garnered much well deserved respect and praise. However, Status has adapted the work to suit the distributed nature of the messaging protocol used.
Perfect forward secrecy is designed to protect your old and future messages even if the private keys to current messages are stolen and encryption is compromised. As described above, end-to-end encryption protects your messages from intermediaries. But what if those keys are in fact compromised? Not only would the current message be readable, but all previous and future messages would be as well. Well, not with perfect forward secrecy.
Perfect forward secrecy was made popular by the people behind the Signal protocol as a means of future proofing message privacy. With pfs, keys used to encrypt and decrypt messages are frequently changing - so if the latest keys are compromised, all previous and future messages will be safe and only a small amount of data is deemed unprivate.
Using a system called "double ratchet," new encryption keys generate with every message – even those sent consecutively by the same person. Therefore past messages cannot be decrypted by a third-party who manages to get a hold of a single message’s private key.
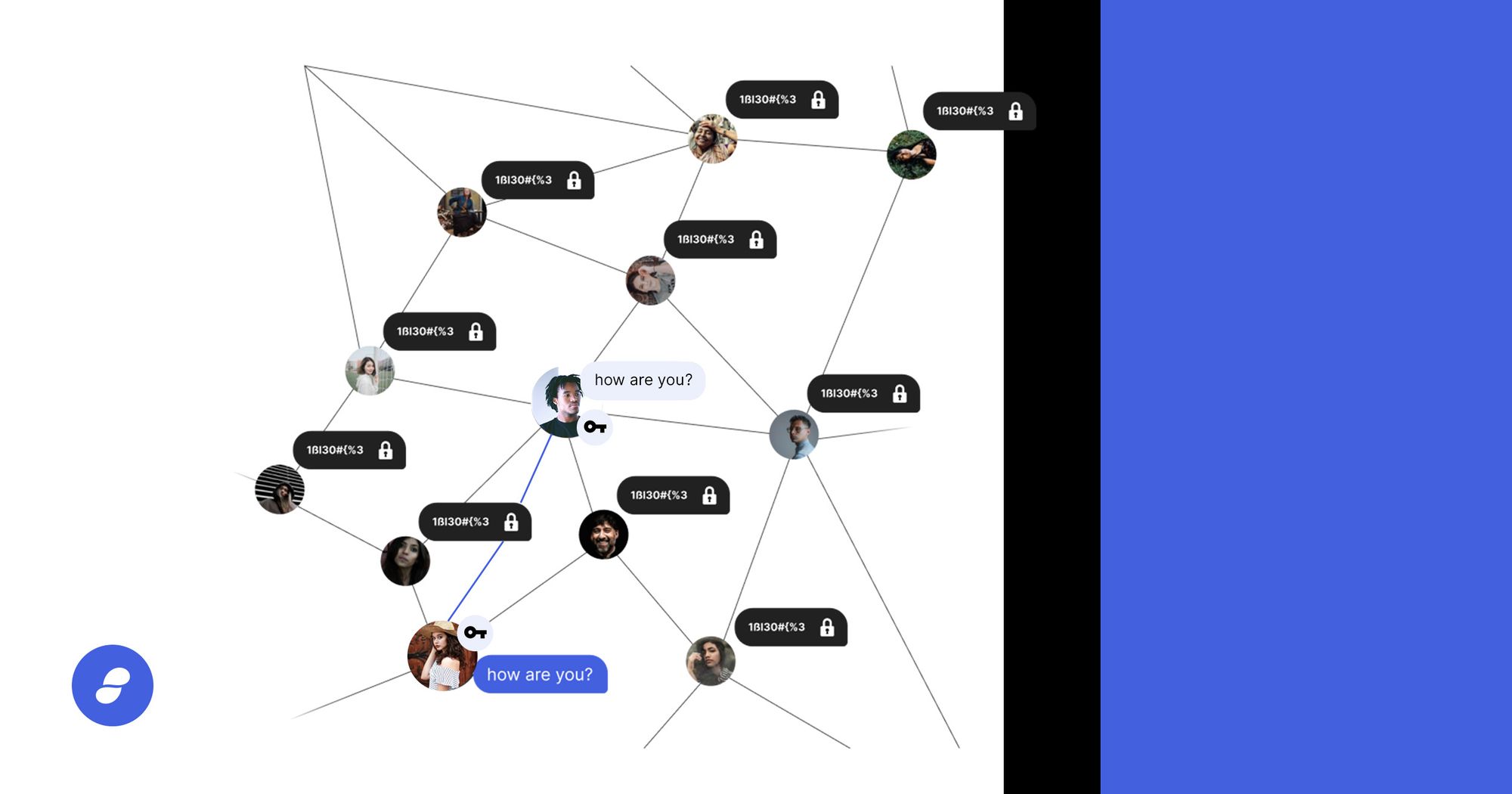
In simple terms, peer-to-peer messaging removes the need for centralized third party servers to pass messages throughout a network. In traditional client-server networks (in use by most major messaging apps today), messages are sent from person A to a central server in the network for processing and then forwarded on to person B.
These servers host and process all messages in the network leading to major privacy and security risks as they become single points of failure and centralized attack vectors. Even with advanced forms of end-to-end encryption and other privacy measures, these centralized servers present risks.
There are a few different types of peer-to-peer messaging networks in use today including onion routing, TOR, and gossip-based communication protocols such as Waku.
In the case of Waku, which is used in Status, when person A wants to send a message to person B, she broadcasts it to multiple nodes in the network, and that message bounces from node to node, ending up with Bob. All messages are end-to-end encrypted by default so only the intended recipient, Bob, can unlock and view the contents of the message.
It is important to note that Status and Waku are not entirely peer-to-peer yet as mailservers are used to manage messages when a peer is offline. A Waku mailserver is a Waku extension that stores messages and delivers them when the peer comes back online. The long term goal is to remove the need for mailserves all together. For more information on mailservers, check out the Status spec.
In short, peer-to-peer messaging aims to deliver:
- 1Removal of traditional centralized intermediaries
- 2Decentralization of the network and removal of single points of failure
- 3Censorship resistance
Most messaging apps require some form of third party validation when creating an account – often a phone number, but sometimes an email address or even a bank account. This enables the messaging service, WhatsApp for example, to create a user id and connect you to your peers. Also, the recoverability of the account is oftentimes dependent on the users phone number.
In the case of messengers that require a phone number, you are typically required to share your phone number with anyone you chat with. Removing separation between private mobile phone numbers and your app identity.
While this is a convenient way to connect and grow the network, it instantly associates an account to very public third party identification. And one step further, phone numbers are easily compromised and taken over by corporations that distribute them.
Status does not require a phone number, email address, or bank account to create an account. Instead, users will choose a randomly generated 3-word name during the onboarding process such as `Lavender Trivial Goral`. This random 3-word name will become the Status identity unless the user purchases and uses an ENS username – rendering Status a pseudo-anonymous platform and the ability for the user to selectively disclose what information they want.
Open source code does not render the features of messaging apps any more private, but it does help to create a more secure overall end product. Open source software can be reviewed, critiqued, changed, altered, and modified by anyone in the world. As Linus Torvalds said: “Given enough eyeballs, all bugs are shallow.”
So look for messengers in which the code is all open source and available for peer review. This doesn't mean that you have to go review it for issues and vulnerabilities (but you can!). It simply means that someone with expertise in the field can.
With surveillance on the rise and a massive financial incentive for organizations of all types to extract personal data, finding means of preserving our privacy is crucial. Choosing a private, secure messenger is one way to do so. Of course some of the features mentioned above come with tradeoffs, but when building Status, each one of these was a critical requirement before releasing v1 in the App and Playstore.
We understand there are some highly requested features noticeably missing from this list such as self detonating messages. And as mentioned above, this is not the only way to approach private messaging – it is simply how Status has approached and we continue to research and develop additional ways to ensure the highest level of privacy possible. After all, we truly believe that through privacy, we can collectively preserve culture.
Finally, it is important to note that many privacy centric features come with trade offs including efficiency and scalability. With continued R&D through work on the Status app, Vac, Nimbus and others, we hope to solve some of these issues in an iterative fashion.
Use a private messenger now and install Status here in the App Store, Playstore, and via APK.
Learn more about all the features of Status including the private messenger, secure crypto wallet, and web3 browser here
*Update to the original graphic. Telegram client is open source while the servers are not. Updated graphic to state "App & Server Completely Open source"