
Messaging is a critical Status component. The Status app combines peer-to-peer messaging technologies with robust end-to-end encryption across all your devices. Peer-to-peer messaging eliminates the need for centralized servers and intermediaries, providing a censorship-resistant alternative to other popular messaging apps.
We've built the Status app to keep your messages and information out of our reach. Other messaging apps offer end-to-end encryption, but their centralized network design allows interpretation of who is talking to whom and where. See how Status compares to other messaging apps in the table below:
| Privacy feature | Status | Other messaging apps |
|---|---|---|
| End-to-end encryption | ||
| Network metadata encryption | ||
| "Who talks to who" encryption | ||
| Censorship resistant | ||
| Anonymous | ||
| Open source |
( available, available on some apps, not available)
- Your messages and data are end-to-end encrypted by default.
- Your messages and data are not stored on any centralized servers.
- Only you and the message recipient can read your messages.
- Status can't identify you or the people you're talking to.
Status provides resilient messaging without relying on centralized servers, data centres, or service providers. The Status app uses Waku, a peer-to-peer protocol for private, secure and censorship-resistant communication.
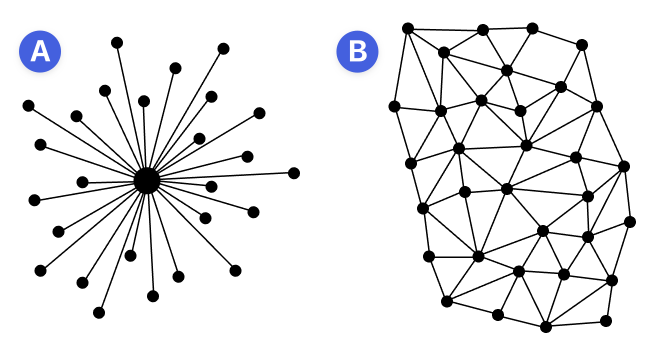
Unlike centralized networks (A), which rely on a centralized server to send messages, peer-to-peer networks (B) encrypt and broadcast every message to all participant nodes. A node is a computer or smartphone that relays messages to other nodes or temporarily stores them for disconnected peers. Even when all nodes can access your messages, the content is encrypted so that only you and the intended recipients can read them.
The Status app secures your messages using end-to-end encryption. This industry standard protection uses strong encryption keys and makes sure that only you and the recipients can read your messages. No one else (not even Status) can read your conversations or identify you or other participants.
When you talk to someone on Status, your messages, attachments, sender metadata, group chats and group chat metadata are all end-to-end encrypted.
Status uses the Perfect Forward Secrecy (PFS) encryption mechanism, ensuring that encryption keys change on every message. If your keys are compromised, only the message they were used for is compromised. All other messages remain private.
